IPad VS Android tablets
 Security always starts with a solid foundation – for tablets, this means each mobile device and operating system’s security architecture.
Security always starts with a solid foundation – for tablets, this means each mobile device and operating system’s security architecture.
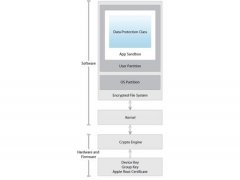
The Apple iPad employs various system security measures to ensure tablet integrity, including a secure boot chain (verifies bootloader, OS kernel, and firmware authenticity), system software personalization (prevents OS downgrade), application code signing (prevents execution of code not reviewed and signed by Apple), an encrypted file system that maintains strict separation between user and OS partitions, and application sandboxing (stops programs from accessing each other’s code and data).
These measures have made it difficult for iOS malware to blossom. Moreover, Apple reviews all code submitted to the iTunes AppStore to ensure proper use of only authorized APIs. Public and enterprise app developers must sign their apps with certificates issued by Apple, and users cannot install unsigned apps without first “jail breaking” their iPad (that is, over-writing Apple’s kernel with an alternative OS that relaxes these native security measures).
iPad apps cannot run as true background processes and cannot access privileged system resources like telephony services. All apps have the same degree of access to shared resources such as network connections, microphone, and camera, but users must decide whether each app should be granted access to location and notifications or send texts or email messages. In iOS 6, contacts, calendars, reminders, and photos were added to this “opt in” permissions list, further reducing private data exposure.
With Android, Google and the Open Handset Alliance took the opposite approach by creating an open OS to run on devices manufactured by many equipment vendors, including Samsung, Motorola, and HTC. Each OEM decides how to protect its own bootloader and firmware, resulting in vulnerabilities that vary by device make/model. This platform diversity creates an uneven playing field, forcing both broadband network operators and IT pros to assess low-level exploits for each kind of Android tablet.
Like iOS, Android kernel security is based on application code signing and sandboxing. Each Android app runs as its own process inside a virtual machine that prevents apps from reading or modifying OS or other application data. But unlike iOS, Android lets apps search for and invoke other apps and run as true background processes – capabilities that can be extremely useful but abused by trojans. In addition, Android apps can freely read/write to shared SD storage found on many tablets, including the Galaxy Tab 2 10.1.
While Android’s security architecture is a bit more relaxed than iOS 6, malware has really been fostered by the free-wheeling Android eco-system. Unlike Apple, Google does not rigorously review code submitted to its Play Store. Instead, Android relies on the open source community to report malware, augmented by Bouncer scans used by Google to find and uninstall already-published malware. Although Android developers must digitally sign their apps, signing certificates can be issued by anyone (even the developer).
Android apps may also be installed from unofficial sources – this risky side-loading practice has been responsible for spreading most Android malware to date. “Rage in the cage” malware even gained root access to system resources and data, neutralizing normal Android app restrictions. Some Android users also root their own tablets to upgrade their OS or install carrier-banned apps.
Android’s security is further weakened by a granular a la carte permissions model in which every app must request a lengthy manifest of rights at install time. In principal this is an asset, but in practice most users just OK their way past that techno-babble to install apps they shouldn’t really trust, published by developers they don’t really know.
Winner: Apple iPads.
Apple runs a tighter ship when it comes to platform security by maintaining tight-fisted control over hardware, iOS, and the iTunes AppStore eco-system. This closed proprietary approach better protects iPads from poorly written or malicious applications, albeit while forcing IT to place considerable trust in Apple. On the other hand, Google is rumored to be working on a Security-Enhanced Linux (SELinux) upgrade to neutralize Android malware that exploits root access.
Source: www.tomsitpro.com






